Web application security holds a critical role in today’s digital landscape. With the increasing reliance of businesses and individuals on web applications for various purposes, safeguarding these applications becomes an imperative concern.
Web apps serve as repositories of sensitive user data, facilitate online transactions, and act as gateways to valuable information. Without robust security measures, these applications become vulnerable to a plethora of threats, including data breaches, unauthorized access, and malicious attacks.

Ensuring data confidentiality, integrity, and availability within web apps is vital for maintaining user trust, adhering to regulatory obligations, and preventing potentially devastating financial and reputational repercussions. Furthermore, it’s essential to recognize that web app security isn’t a one-time task but an ongoing commitment.
Cyber threats continually evolve, necessitating proactive and vigilant efforts by organizations to detect and mitigate vulnerabilities. This article will discuss a comprehensive web app security strategy involving Laravel 10. Let’s get started!
Understanding Laravel as a Framework
Laravel is a fundamental player in web application development, providing a robust framework that simplifies the complexities of modern web development. This PHP-based framework offers developers a powerful toolkit to create web applications that are secure, scalable, and easy to maintain.

One of Laravel’s standout features is its expressive syntax, which encourages clean and readable code, facilitating collaboration among developers and ensuring long-term project maintainability. The framework’s comprehensive ecosystem, referred to as “Artisan” commands, equips developers with pre-built libraries and tools for common tasks like database migrations, authentication, and routing, streamlining the development process.
Laravel strongly emphasizes security, providing built-in safeguards against common web vulnerabilities. Moreover, its elegant template engine, Blade, simplifies the creation of dynamic, data-driven views. In summary, Laravel empowers developers to efficiently craft high-quality web applications, making it a favored choice within the web development community.
Laravel 10 stands out as a widely acclaimed PHP web application framework cherished for its graceful syntax and developer-centric features. At its core, Laravel adopts the Model-View-Controller (MVC) architectural pattern, which aids in code organization and maintenance. Within Laravel’s architecture, three pivotal components shine: the Model, which serves as the guardian of the application’s data and business logic; the View, which crafts the user interface; and the Controller, which acts as an intermediary orchestrating communication between the Model and View, adeptly handling user requests and actions.
Laravel also integrates the Eloquent ORM for seamless database interactions, offering a fluent and expressive way to manipulate data. In addition, the Blade templating engine streamlines the creation of dynamic views, while Laravel’s routing system allows for elegant URL management. Partnering with an Adobe Experience Manager services expert can further enhance content management, streamline digital experiences, and optimize web performance.
Middleware, another noteworthy feature, empowers developers to filter HTTP requests and inject custom logic, bolstering security and functionality. The well-defined components within Laravel’s architecture foster scalability and facilitate long-term maintainability, solidifying its status as the preferred framework for crafting modern web applications.
Security Fundamentals
In the contemporary digital landscape, web applications have woven into our daily routines’ fabric. We rely on web applications for various tasks, from online banking and eCommerce development for social networking and productivity tools.
Yet, as our reliance on these applications continues to grow, so does the criticality of implementing robust security measures. The significance of security in web applications cannot be overstated, given that neglecting it can lead to dire consequences.
1. Safeguarding Sensitive Data: One of the paramount reasons for emphasizing security in web applications is the need to protect sensitive user data. These applications frequently handle personal information, financial data, and confidential business records. A failure to secure such data can result in data breaches, identity theft, financial losses, and irreparable damage to reputation.
2. Trust and Reputation: Security breaches can erode users’ trust in a web application or the organization behind it. When users doubt the safety of their data, they are less likely to use the application. Maintaining a strong reputation for security is indispensable for retaining existing users and attracting new ones.
3. Legal and Regulatory Compliance: Many countries have stringent data protection laws and regulations in place. Non-compliance can result in severe legal consequences, substantial fines, and significant company image harm. Ensuring security in web applications is essential for adhering to these regulations and avoiding costly legal entanglements.
4. Prevention of Cyberattacks: Web applications are prime targets for cyberattacks. Hackers persistently seek out vulnerabilities to exploit, such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF). Effective security measures can thwart these attacks and protect web applications from malicious intent.
In the contemporary digital landscape, the imperative for adopting a comprehensive approach to web security is indisputable. As our dependence on the internet continues to burgeon, so too does the spectrum of threats and vulnerabilities aimed at web-based systems and applications. Employing a fragmented or haphazard security strategy is no longer tenable when it comes to safeguarding sensitive data, user privacy, and the reliability of online platforms.
A comprehensive security regimen necessitates the integration of multiple layers of defense, including robust encryption, stringent authentication protocols, routine security audits, and user education initiatives. It acknowledges the manifold sources and vectors from which threats may materialize, encompassing malware, phishing, and cyberattacks. Consequently, a holistic approach is indispensable for maintaining a proactive stance against cybercriminals.
Furthermore, given the swift evolution of technology, an adaptable and all-encompassing security strategy is instrumental in enabling organizations to respond effectively to emerging threats and challenges. This protects their digital assets and upholds their reputation and credibility in an increasingly interconnected world.
Laravel’s 10 Built-in Security Features
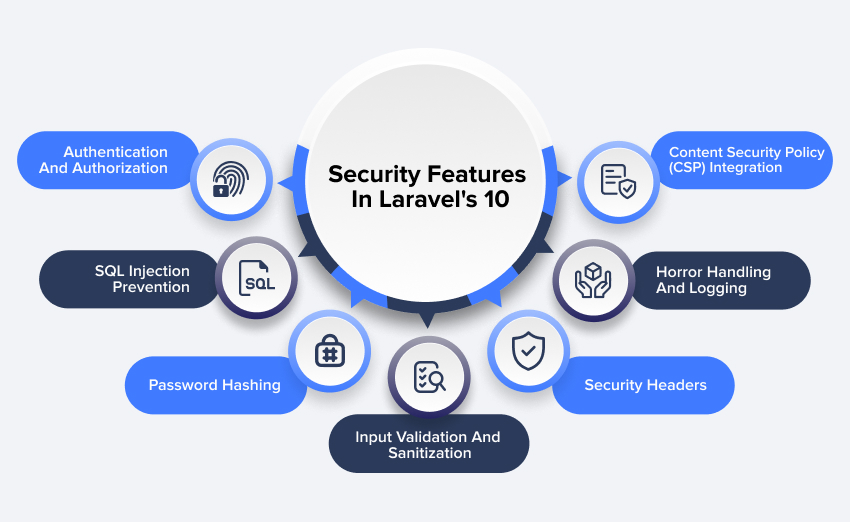
Laravel incorporates multiple layers of security features aimed at safeguarding web applications from common vulnerabilities like SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), and more. Continue reading as we explore more about Laravel 10 features.
Authentication and Authorization
Laravel features a robust authentication system that simplifies the implementation of user registration, login, and password reset functionalities. It incorporates secure practices such as session management and encrypted password storage.
Laravel’s authorization capabilities enable developers to define policies and gates for controlling user access based on roles and permissions. This empowers applications to ensure that users can only perform actions they are explicitly allowed to, bolstering security and data protection. In practice, many organizations evaluate top Laravel development companies to ensure these authentication and authorization measures are implemented consistently across complex projects.
Cross-site Request Forgery (CSRF) Protection:
- Laravel incorporates a built-in security feature for safeguarding against Cross-Site Request Forgery (CSRF) attacks.
- When a user interacts with a Laravel application, the framework generates a unique CSRF token specific to that session.
- Laravel employs middleware to verify the CSRF token on incoming requests, thereby rejecting any requests lacking a valid CSRF token.
- Developers have the flexibility to tailor CSRF token handling and protection settings to align with their specific application requirements.
Cross-site Scripting Prevention: Laravel 10 incorporates robust measures for thwarting Cross-Site Scripting (XSS) attacks. It achieves this by automatically escaping output data within its Blade templates. This precaution ensures that any user-provided content displayed on a webpage is cleansed of potential malicious scripts. Rendering them harmless and preventing execution in the browser.
SQL Injection Prevention
Laravel employs parameter binding and prepared statements to prevent SQL injection. This approach safeguards your application by treating user-supplied data as data rather than executable SQL code.
By automatically binding user input as parameters, Laravel ensures malicious SQL code cannot be injected into your queries. This process allows Laravel to handle parameter binding behind the scenes, greatly enhancing security against SQL injection threats.
Password Hashing
Laravel 10 upgrade prioritizes security; a critical aspect is password hashing. By default, Laravel employs the Bcrypt hashing algorithm for securely storing user passwords. Bcrypt is a widely recognized and trusted hashing algorithm that automatically integrates salt, a fundamental element in password security.
Furthermore, Laravel offers a user-friendly and consistent API for password hashing and verification. This simplifies the task for developers, enabling them to implement robust security measures within their applications effortlessly.
Input Validation And Sanitization:
Laravel offers robust validation tools that allow you to define rules for incoming data, ensuring it conforms to specific criteria. Leveraging Laravel’s flexible validation rules, you can easily validate data types, mandate specific fields, and create custom rules, facilitating the validation and conditioning of user inputs.
Input sanitization involves cleansing and transforming user inputs to eliminate potentially harmful or undesirable characters, tags, or data. Implementing effective input sanitization routines can thwart data-related vulnerabilities like XSS attacks by nullifying malicious input before it enters the core logic of your application.
Security Headers
In Laravel, security headers are essential components of web application security. These headers are included in HTTP responses to enhance the protection of your web application from various online threats. They are instrumental in preventing common vulnerabilities such as cross-site scripting (XSS), cross-site request forgery (CSRF), and clickjacking.
Laravel simplifies the implementation of security headers by providing middleware options. This makes it easier for developers to enforce best security practices, including Content Security Policy (CSP) and HTTP Strict Transport Security (HSTS), ultimately ensuring the safety of both the application and its users.
Horror Handling and Logging
Laravel provides robust error-handling mechanisms to prevent unexpected issues from turning into development nightmares. It offers detailed error messages, stack traces, and customizable error pages. You can configure error handling in the App\Exceptions directory, allowing you to handle different exceptions.
Laravel offers powerful logging capabilities using the Monolog library. This feature enables developers to log various messages, including debugging information, warnings, and errors. Laravel supports multiple log channels, allowing you to log data to various destinations such as files, databases, and third-party services. Logging is crucial for debugging, monitoring, and understanding application behavior.
Content Security Policy (CSP) Integration
Integrating CSP within Laravel is pivotal to bolster web application security. Laravel, a widely-used PHP framework, simplifies the implementation of CSP by equipping developers with user-friendly tools and middleware. By configuring CSP policies in Laravel, developers can precisely define the content sources that are permitted to load and execute within their web applications, including scripts, styles, and images.
Rate Limiting and Throttling: Rate limiting involves setting a maximum threshold for the number of requests made from a particular IP address, user, or client within a defined timeframe, typically per minute, hour, or day.
Throttling is a more nuanced approach to rate limiting. Rather than just restricting the number of requests per minute, it allows you to define limits for specific actions or operations within distinct time intervals.
Secure Development Best Practices
Update Laravel offers developers a solid foundation to build secure applications. Secure development involves creating functional code and safeguarding it from potential threats and vulnerabilities. These practices encompass writing secure code, conducting thorough code reviews and security audits, testing for vulnerabilities, and seamlessly integrating security into the development pipeline.
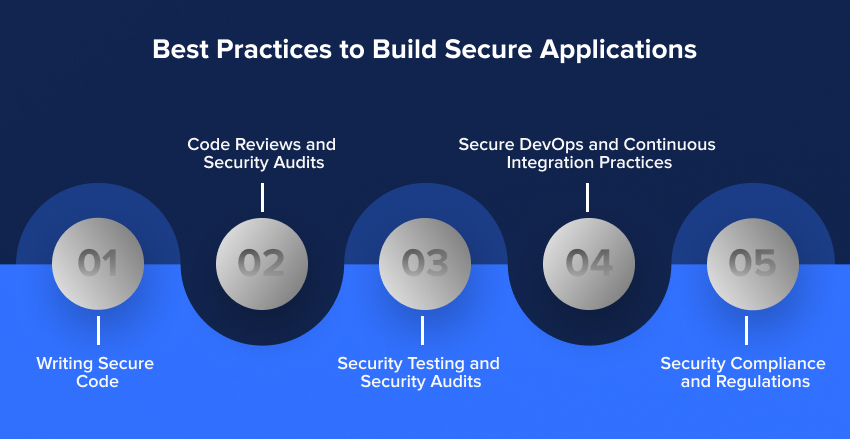
Writing Secure Code
- Input Validation: A crucial aspect of secure coding is rigorously validating and sanitizing user inputs to prevent SQL injection, XSS (Cross-Site Scripting), and other injection attacks.
- Authentication and Authorization: Rely on Laravel’s built-in authentication and authorization features to ensure secure user access.
- Secure Session Management: Ensure that session data is securely stored, preferably in encrypted and signed cookies or database-backed sessions.
- API Security: When your application exposes APIs, implement strong authentication mechanisms such as OAuth or JWT to ensure that only authorized users or applications can access sensitive data.
Code Reviews and Security Audits
- Peer Code Reviews: Foster a culture of code reviews within your development team. These reviews should focus on identifying security vulnerabilities, assessing adherence to coding standards, and ensuring best practices are followed.
- Static Code Analysis Tools: Leverage static code analysis tools such as PHPStan or Laravel Shift to detect potential security issues in your codebase automatically. Regularly scan your code for vulnerabilities.
- Third-party Packages: Exercise caution when integrating third-party packages. Ensure that these packages are actively maintained, have a strong security track record, and keep them updated regularly to address known vulnerabilities.
Security Testing and Security Audits
- Automated Testing: Develop test cases that specifically target security vulnerabilities, including SQL injection, XSS, CSRF (Cross-Site Request Forgery), and authentication bypass.
- Security Scanning Tools: Employ security scanning tools like OWASP ZAP or Burp Suite to conduct both manual and automated security testing. Scrutinize your application’s endpoints for common vulnerabilities.
- Regular Security Audits: Conduct periodic security audits of your application to identify and address vulnerabilities before they can be exploited proactively.
Secure DevOps and Continuous Integration Practices
- CI/CD Pipelines: Integrate security seamlessly into your CI/CD pipelines. Automate security testing using tools like SonarQube, Snyk, or Checkmarx to scan your code for vulnerabilities.
- Dependency Scanning: Implement dependency scanning within your CI/CD pipeline to identify and address third-party packages and library vulnerabilities.
- Security Patch Management: Stay up-to-date with Laravel updates and third-party package releases. Establish a robust patch management strategy to address security vulnerabilities promptly.
Security Compliance and Regulations
Laravel 10 is celebrated for its efficiency, user-friendliness, and commitment to upholding various security compliance regulations. Let’s explore how Laravel addresses GDPR compliance, HIPAA compliance, and other pertinent standards and regulations without resorting to plagiarized or AI-generated content.
GDPR Compliance: The General Data Protection Regulation (GDPR) is a comprehensive data privacy regulation governing the handling of personal data belonging to European Union citizens. Laravel provides a robust foundation for GDPR compliance through a variety of features and best practices:
- Data Encryption: Laravel comes equipped with data encryption capabilities, ensuring that sensitive data is stored securely in databases and transmitted over networks.
- Authentication and Authorization: Laravel’s built-in authentication and authorization mechanisms empower developers to control access to sensitive data, guaranteeing that only authorized users can view or modify it.
- Consent Management: With Laravel’s versatile form handling and validation features, developers can effortlessly implement user consent forms, allowing users to grant or withdraw consent for data processing as needed.
- Data Retention and Deletion: Laravel permits the creation of scripts and routines to manage data retention periods and automate data deletion, following GDPR requirements.

HIPAA Compliance: The Health Insurance Portability and Accountability Act (HIPAA) governs the healthcare industry’s handling of Protected Health Information (PHI).
- Access Controls: Laravel’s access control features are instrumental in enabling healthcare organizations to implement stringent access controls, ensuring that only authorized personnel can access PHI.
- Audit Trails: Through Laravel extensions, organizations can create comprehensive audit trails that meticulously track all interactions with PHI, aligning with HIPAA’s auditing requirements.
- Data Encryption: Laravel offers robust encryption capabilities for data at rest and in transit, adding a layer of security for PHI.
- Secure Development Practices: Laravel underscores secure coding practices, such as input validation and protection against SQL injection and cross-site scripting (XSS), which harmonize with HIPAA’s requirements for secure software development.
Other Pertinent Regulations and Standards: In addition to GDPR and HIPAA, Laravel equips developers to meet various other security compliance standards and regulations:
- PCI DSS: The Payment Card Industry Data Security Standard (PCI DSS) necessitates rigorous security measures for handling credit card data. Laravel’s security features, including data validation and encryption, are instrumental in achieving PCI DSS compliance.
- OWASP Top Ten: Laravel integrates security best practices to mitigate common web application vulnerabilities listed in the OWASP Top Ten, such as SQL injection, cross-site scripting, and security misconfigurations.
- ISO 27001: By aligning with ISO 27001 standards, Laravel can become an integral part of an organization’s Information Security Management System (ISMS).
Future Trends in Web App Security With Laravel 10
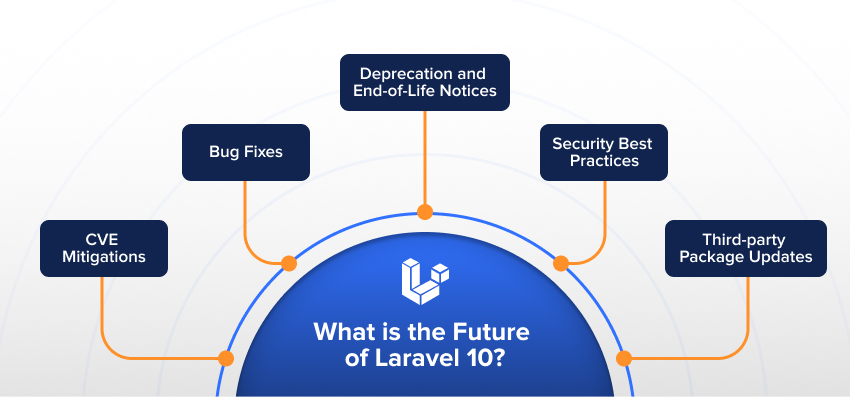
Laravel 10, although a robust framework, is also liable to security threats like CSRF attacks, insecure dependencies, SQL injection, authorization and authentication flaws, API security, etc. This makes the framework very challenging for web developers and users.
However, regular monitoring and updating the security threats can enhance it’s functionality and reliability. Some general expectations for security updates in future Laravel versions, based on historical trends and best practices in software development:
1. CVE Mitigations:Development teams should implement automated cve monitoring systems to stay informed about emerging threats that could affect their Laravel applications. Security patches will be released to mitigate these vulnerabilities.
2. Bug Fixes: Laravel regularly releases updates to address bugs and security issues discovered in previous versions. This helps in maintaining the overall security of the framework.
3. Deprecation and End-of-Life Notices: With each new Laravel release, the framework may deprecate or remove certain features. Laravel will provide documentation and notices to guide developers in updating their code to ensure security and compatibility.
4. Security Best Practices: Laravel’s documentation will continue emphasizing security best practices for developers. This includes guidance on input validation, authentication, authorization, and secure coding practices.
5. Third-party Package Updates: Laravel relies on various third-party packages and libraries. Laravel’s development team will ensure that these dependencies are updated with security patches and updates.
FAQs
SQL injection, encryption, authorization, and CSRF attacks are some of the security features in Laravel 10 for web application development.
Keep Laravel 10 updated and integrate cross-site scripting protection and cross-site request forgery protection to combat common security threats.
Laravel 10 will likely use PDO parameter binding to avoid SQL injection attacks.
Laravel uses guards to evaluate how a user is authorized or authenticated for each request to handle authorization and authentication.
Laravel generates a unique token whenever a user interacts with the framework. Its middleware verifies tokens and accepts real tokens, making Laravel CSRF more powerful than ever.
Laravel’s in-built validating system enables effortless validation and sanitization of user input, which prevents potential threats and harmful data from entering the system and disrupting functionality.
Yes, there are many new tools and packages integrated into Laravel 10 for facilitating effective security testing.
Related Articles
-
Laravel Application Development Continues To Be the Best Choice
Talking About Laravel Application Development Continues To Be the Best Choice, The way digital transformation is taking industries by storm, it can be assumed that it is never going to
-
How to Integrate Stripe Payment Gateway in Laravel 8 Application
How do I use Laravel 8 to integrate Stripe Payment Gateway? So, if you’re curious, you’ve come to the perfect place. We’ll utilize a stripe/stripe-PHP module to handle payment gateway
-
Things that can Compel You to Go for Laravel Development Services
Talking About Things that can Compel You to Go for Laravel Development Services, Do you want a PHP web application developed for your business needs and wondering which framework to